











Reimagining mortgage distribution
We create powerful software, data and analytics that unites lenders, brokers and aggregators to operate compliantly and efficiently, giving borrowers certainty earlier in their search for a mortgage.
Our Integrated Solutions
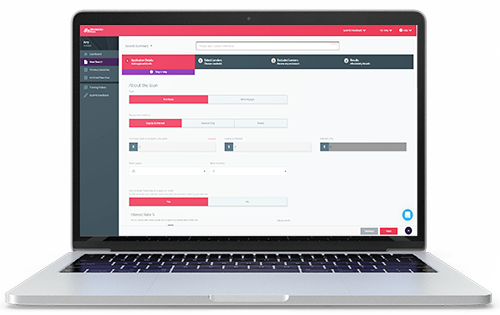
With over three decades in the industry, Mortgage Brain is well positioned to reimagine the industry plumbing - the way mortgage products are sourced and distributed. Our mortgage broker software offers streamlined, simple, and efficient solutions for mortgage intermediaries, lenders, and business partners throughout the whole mortgage process.

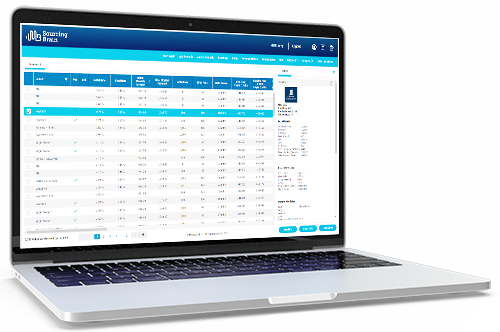
Lender Service Report
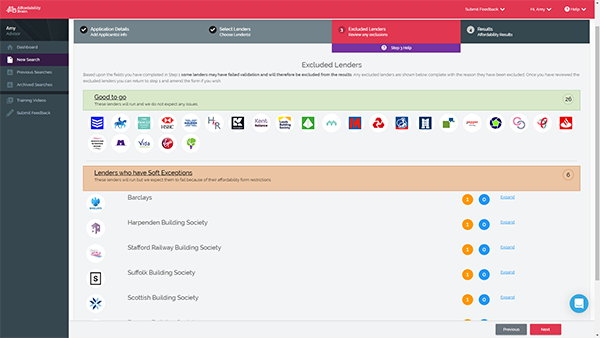
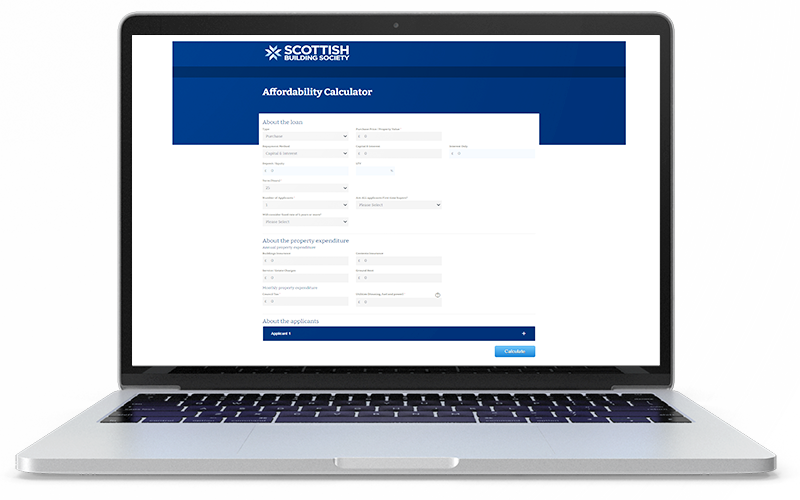
Whether you’re a mortgage adviser using our mortgage broker software or a lender, the Lender Service Report is a handy tool that is updated fortnightly. It’s a central point that gives a snapshot of the state of lender service levels across the industry. A quick look tells you the sort of waiting times you can expect for different aspects such as case updates, general response times, initial assessment, and time to offer for both residential and buy-to-let.
For mortgage advisers, it means you quickly make recommendations and set clear expectations without spending time visiting each lender’s website.
For lenders, it’s an easy way to gauge how your service levels are performing against those of your competitors.
testimonials